Everything from manufacturing plants to power grids relies on operational technology (OT) to operate efficiently, safely, and profitably. But as businesses increasingly rely on OT, the impact of security breaches has escalated. Cyberattacks targeting OT grew by 140% in 2022, impacting over 150 industrial organizations.1 As these attacks increase, analysts expect cyber threats may shut down 15,000 industrial sites throughout 2028.2
Unfortunately, attacks targeting OT systems often yield consequences beyond operational delays. Some significant OT security incidents in 2022 resulted in:1
- A fire resulting in material equipment damage during an attack on a mining company.
- Malfunctions while loading and unloading cargo, fuel, and bulk oil at six seaports on three continents.
- Delayed flights for tens of thousands of passengers when four air travel companies suffered attacks.
With OT forming the foundation of critical infrastructure and revenue generation across industrial industries, securing these systems is no longer optional – it's imperative. In this blog, we’ll explain what OT is, how it differs from information technology, and why modern businesses need to prioritize IT and OT security alike to remain competitive.
What Is Operational Technology?
OT is the hardware and software systems used in industrial processes like those found in manufacturing, energy, oil and gas, robotics, and other industrial industries. OT includes technologies such as:
- Industrial Control Systems (ICS), which manage and automate industrial processes like manufacturing, product handling, and utilities.
- Supervisory Control and Data Acquisition (SCADA) Systems, which collect sensor data and control geographically distributed assets.
- Distributed Control Systems (DCS), which provide automation and control within a localized process system.
These technologies interact with physical equipment like valves, switches, motors, pumps, and more. OT systems emphasize safety, availability, reliability, and consistent uptime – and any downtime can severely impact operations and profitability.
What Is Information Technology?
Information technology (IT) refers to the computing systems that store, send, and receive data. For businesses, IT primarily focuses on software, networks, and computer equipment that enable communication and productivity. Common IT systems include:
- Laptops, desktops, smartphones, tablets, and peripherals
- Servers, storage systems, and networking equipment
- Cloud platforms and web-based software
- Operating systems, business applications, and databases
While uptime is important for IT, the top priority for IT teams is typically protecting the confidentiality and integrity of data on these systems.
What Are the Differences Between OT and IT?
OT and IT serve distinct purposes within an organization and have significantly different priorities. OT systems are designed to support and control physical devices and processes in industrial environments, such as manufacturing plants, utilities, and oil/gas facilities. The primary goal of OT is ensuring the safe, continuous operation of machines to efficiently produce products or deliver services.
The top priorities for IT are maintaining the confidentiality, integrity, and availability (the CIA triad) of data and information assets. While uptime is important, IT's main focus is preventing data breaches, loss of sensitive information, and disruptions to computing services.
OT and IT networks also differ considerably in their design principles. IT networks typically incorporate security segmentation, identity and access management controls, and extensive logging/monitoring capabilities. Traditional OT networks, however, were designed without segmentation so personnel could access systems from anywhere to provide support and monitoring.
Why Do Businesses Need Security for OT and IT?
A 2023 survey found that 32% of industrial organizations fell victim to a ransomware attack, while malware intrusions increased by 12%,3 highlighting the need for industrial organizations to secure OT and IT systems alike.
OT systems control processes that keep businesses operational, while IT systems contain sensitive data like intellectual property, customer information, and financial records. When this data is compromised during a cyberattack, businesses face catastrophic financial and reputational damage. As OT systems become more interconnected with IT systems, cybercriminals are gaining new vulnerabilities to exploit and infiltrate industrial networks.
What Is OT Security?
OT security focuses on safeguarding the technologies that control and automate physical industrial processes. Core goals include:
Ensuring System Availability
Keeping OT systems available and reliable during operations is essential, as unplanned outages directly halt production and revenue generation. Solutions that support asset availability include redundancy, resilience against disruptions, and disaster recovery capabilities.
Protecting Against Unauthorized Access
Safeguarding OT devices and networks from unauthorized users helps prevent cyberattacks and data breaches. Measures like authentication, network segmentation, and secure remote access controls limit pathways for malicious parties.
Guarding Against Malware
Industrial malware can manipulate and disrupt OT processes. Anti-malware defenses tailored to control systems and robust patching and anomaly detection tools provide multilayered protection against infection.
Enabling Secure Remote Access
Personnel often need remote access to OT infrastructure for monitoring and maintenance. Secure remote access technologies balance connectivity and control without increasing attack surfaces.
Segmenting OT Networks
Isolating OT networks from other environments helps contain threats and mitigates lateral movement after a data breach. Network segmentation also facilitates monitoring across trust zones.
Detecting Anomalies
Collecting and analyzing OT system data allows security teams or automated tools to detect potential cyberattacks or process abnormalities faster. Machine learning algorithms can use this system data to identify variants from baseline operations.
Maintaining Regulatory Compliance
Following industry regulations like NERC CIP helps ensure OT security for critical infrastructure. Standards may cover areas like system hardening, access controls, and data encryption.
OT Security vs. IT Security
While OT and IT security protect distinct environments, there are key differences in how they achieve this. We break down these differences below:
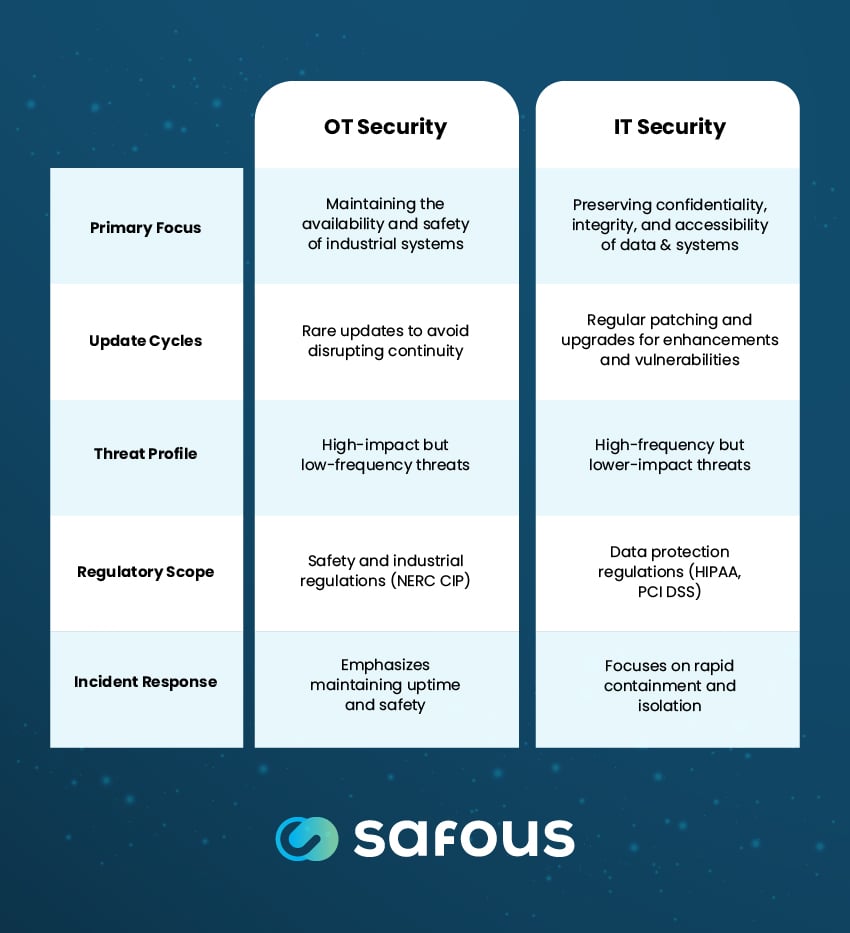
Primary Focus
As disruptions can lead to suspended manufacturing, utility outages, and costly disruptions, OT security's top priority is maintaining the continuous availability and safe operation of industrial control systems that monitor and automate physical processes.
In contrast, IT security prioritizes preserving the confidentiality, integrity, and accessibility of data and information systems. The key focus is preventing data breaches, loss of sensitive information, and disruptions to computing services.
Update Cycles
OT systems rarely receive software and firmware updates since changes can necessitate downtime and disrupt operational continuity. As a result, OT components may continue running outdated or vulnerable versions because downtime for upgrades can affect time-sensitive physical processes.
IT systems are regularly patched, updated, and upgraded to address security vulnerabilities, add new user features, and improve system performance. Rigorous change management processes minimize downtime and service interruptions during IT system updates.
Threat Profile
The highly specialized nature of OT environments limits threats, but they’re increasing in frequency. Threats targeting OT systems are high-impact when successful, often leveraging insider credentials or incremental manipulations that lead to major physical damage over time.
IT threats occur more frequently but have lower impacts per incident, typically exploiting external remote access pathways and malware to steal confidential data. However, the interconnected nature of IT systems can lead to operational downtime during cyber attacks.
Regulatory Scope
Due to the physical safety risks involved in industrial businesses, OT systems must comply with specialized safety regulations, like the NERC CIP cybersecurity standards for North American electric utilities and power generators. Further, OT systems have unique protocols (e.g. Modbus, DNP3) not commonly found in IT environments.
IT compliance regulations revolve around data protection laws like HIPAA for safeguarding health data, PCI DSS for securing payment card information, and various state and federal privacy statutes.
Incident Response
Responding to OT security incidents emphasizes maintaining critical uptime availability and physical safety. However, due to production requirements, isolating or completely shutting down OT systems isn’t always possible. Incident response is usually deliberately cautious and focuses on gradual restoration.
IT security response aims to rapidly contain threats by isolating compromised systems and preventing further data loss, even if it requires shutting down applications and services. Quick action is prioritized to stop threats from spreading across interconnected systems.

Why Do Businesses Need OT Security?
Historically, OT systems operated on isolated, proprietary networks separated from external connectivity. However, the rise of initiatives like Industry 4.0 has accelerated the integration of OT and IT environments, adding IoT sensors, manufacturing analytics, and remote monitoring to connect the once-isolated OT infrastructure.
While this data-driven connectivity can improve process optimization, it also expands the attack surface. General computing devices and operating systems are increasingly used in OT networks rather than specialized industrial components. If unpatched or misconfigured, these provide pathways for external threats to penetrate previously segregated OT environments.
The increased interconnectivity between OT and enterprise IT networks enables bad actors to gain access via compromised IT systems before pivoting to exploit vulnerable OT devices. Damage from successful attacks on vulnerable OT environments often disrupts industrial processes, causing immediate revenue loss and asset damage. And unfortunately, entire supply chains suffer when a single supplier is compromised – resulting in $46 billion in losses last year.4
OT Security Best Practices
Here are some essential best practices industrial organizations should follow to secure your OT environments:
Identify All Connected Assets
You can’t protect what you can’t see. Maintain an inventory of all connected OT systems and components and update it frequently. This comprehensive visibility also makes it easy to execute risk assessments, configure access controls, and monitor your systems.
Segment and Control Network Traffic
Limit network connections to only necessary ones, and monitor traffic for signs of threats. Unmonitored communications between secure and insecure zones enable unauthorized users to move laterally throughout your OT network.
Harden OT Devices
Secure configurations, patch management, and limiting unnecessary services help prevent breaches in vulnerable systems. Hardened devices also minimize risks if compromised by a bad actor.
Monitor for Anomalies
Collect and analyze OT system data to detect potential cyberattacks or process abnormalities rapidly. Machine learning models trained on baseline operations can identify anomalies indicative of emerging threats.
Limit Privileged Access
Only allow essential personnel access to OT networks and devices. Enforce multi-factor authentication (MFA) and limit lateral movement across zones to minimize insiders’ potential impact.
Backup Critical Parameters
Maintain backups of important OT data and configurations to enable rapid restoration during outages or corruption. Backups limit downtime and support forensics during security incidents.

Bolster Your Organization’s OT Security With Safous ZTA
As industrial firms increasingly connect IT and OT systems, robust cybersecurity has become critical. Legacy remote access tools fail to adequately protect OT infrastructure and supply chains. This is where Safous Zero Trust Access provides the modern security solution organizations need.
Safous ZTA is an all-in-one platform that replaces outdated remote access methods while safeguarding OT and IT systems. A key advantage is it does not require connecting your isolated OT network directly to the internet. Instead, the on-premises Safous AppGateway deploys inside your OT network, enabling secure remote access over protocols like HTTPS/SSH – not the public internet. Safous avoids automatically updating customer systems, ensuring operations uptime. Ready to see Safous ZTA in action? Book a demo today.
Sources:
- https://securityintelligence.com/news/high-impact-attacks-on-critical-infrastructure-climb-140/
- https://industrialcyber.co/reports/waterfall-2023-threat-report-detects-ot-cyberattacks-with-physical-consequences-increasing-exponentially/
- https://www.fortinet.com/content/dam/fortinet/assets/reports/report-state-ot-cybersecurity.pdf
- https://cybersecurityventures.com/software-supply-chain-attacks-to-cost-the-world-60-billion-by-2025/
Receive the latest news, events, webcasts and special offers!
Share this
You May Also Like
These Related Stories

What Are Cyber-Physical Systems (CPS)?

How Zero Trust Access Enhances Industrial Secure Remote Access




