If you’re on the hunt for modern cybersecurity tools to protect your business network, you’ve likely come across several security options. While there isn’t a one-size-fits-all solution for network security, many organizations find success using zero trust architecture (ZTA) and privileged access management (PAM) to safeguard their critical assets.
We’ve discussed the benefits of zero trust before, but what does PAM do? Both ZTA and PAM provide organizations with advanced security measures, but they do so in different ways. This blog will explore the differences between these two security models to help you decide if you need both for your business.
What Are the Differences Between ZTA vs. PAM?
Before we can discuss why PAM is so important for network security, we have to take a look at privileges.
When it comes to IT, privileges are defined as the authority an account or process has within a computing system or network. Since privileges provide access to restricted information and administrative functions, such as adding or deleting users and configuring system settings, they are usually only available to users with privileged accounts.
A privileged account is any account with higher privileges than non-privileged accounts. These are often administrator or superuser accounts, which allow the user to install software, change local configurations and settings, and more. Because privileged accounts can access confidential data and secure environments, additional security measures are needed to protect them.
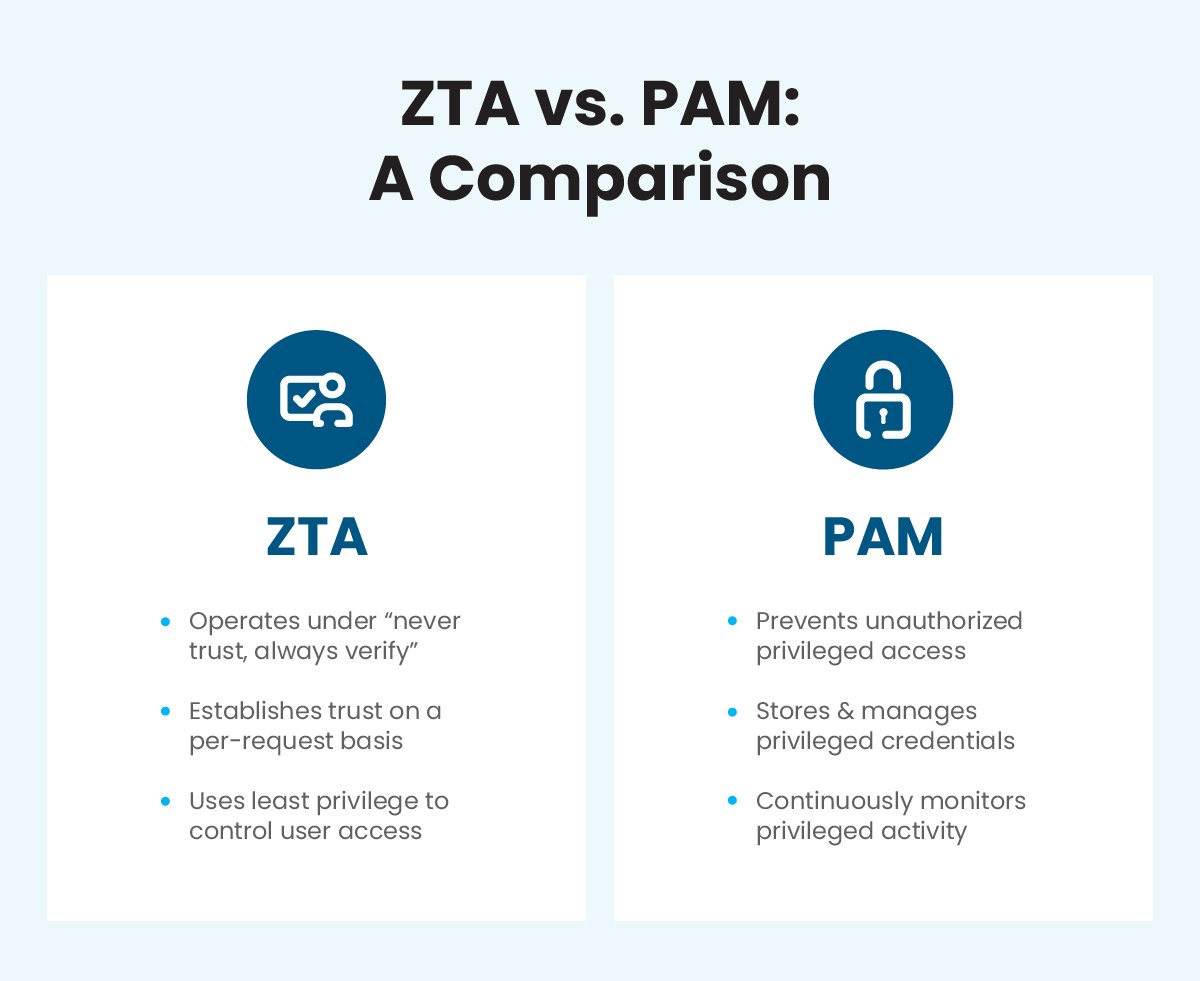
That’s where privileged access management comes in. PAM is a security model that aims to prevent unauthorized access to privileged accounts. Since PAM manages and monitors privileged access to sensitive resources – servers, databases, and critical applications – it can ensure privileged access is only granted to authorized users and isn’t being misused.
A zero trust architecture also provides advanced security measures to safeguard network access, but operates under different concepts. ZTA emphasizes the importance of identity and access management under the default assumption that no user, device, or application can be trusted. It relies on a layered approach that establishes trust on a per-request basis instead of trusting (or sharing privileges with) a user based on location or network.
How Does PAM Differ From the Principle of Least Privilege?
The principle of least privilege is a security concept that says users, applications, or processes should only be granted the minimum privileges necessary to perform their job functions or required tasks. By enforcing this principle across your IT environment, you can define both the scope and duration of privileged access, then automatically revoke access when the user completes the privileged activity.
PAM employs least privilege access to provide the management and oversight needed to mitigate the risks posed by privileged accounts. However, it’s not the only technology businesses can use to enforce the principle of least privilege.
Why Should Businesses Use Both ZTA and PAM?
The zero trust concept of “never trust, always verify” is about controlling access – and with a whopping 80% of data breaches stemming from compromised privileged account credentials,1 it’s clear that unnecessary privileges are the riskiest type of access.
In most cases, cybercriminals try to capture privileged account credentials to gain access to the rest of a business network and the data within it. Once they breach a privileged account, they can move throughout the network without leaving a trace or triggering any alarms. But because PAM stores privileged account credentials in an isolated, monitored environment, unauthorized access becomes virtually impossible to obtain.
While ZTA uses the principle of least privilege to control what users can access once authorized, adding PAM functions can enable businesses to:
- More easily enforce authentication and authorization policies for privileged accounts.
- Continuously monitor access and take immediate action whenever a threat is detected.
- Remediate risky behavior by suspending or terminating privileged access automatically.
- Maintain a complete audit record to satisfy compliance requirements and aid remediation.
- Keep track of all remote and privileged account access and activities in one place.
Keep Your Business Network Secure With Safous
Network security is constantly evolving – especially as more organizations embrace the cloud and hybrid working models. Luckily, there are many cybersecurity tools to help ensure your network and critical data are always secure – without compromising on fast, reliable access for your employees.
Because Safous ZTA incorporates some of the PAM features, Safous can help keep your business network safer than ever with both ZTA and PAM. Our all-in-one ZTA platform strengthens your zero trust security posture and enables privileged access management with integrated multi-factor authentication (MFA) and single sign-on (SSO) security features.
Trust Safous for:
- 24/7 remote monitoring and business support
- Integrated security functions
- Guaranteed regulatory compliance
- High-level authentication and control
- Quick and easy onboarding
- No additional software, plug-ins, or specific OS required
If you’re ready to strengthen your security posture, Safous is here to help. Request a demo today to learn how Safous ZTA and PAM can eliminate network vulnerabilities, prevent breaches, and more.
Sources:
Receive the latest news, events, webcasts and special offers!
Share this
You May Also Like
These Related Stories

Three Data Breach Disasters Caused by Shared Super Admin Accounts

IAM, ZTA, and PAM: How Identity and Access Management Fits into Security




