Secure Remote Access for Industrial OT/ICS Assets
Safous Industrial Secure Remote Access (SRA) extends zero trust security to your OT/ICS security strategy to safeguard the entire industrial environment, so your teams can securely connect people to your infrastructure from anywhere.
The Industrial Sector’s Growing Need for Secure Remote Access
Your Needs
Our Solution
Remote Privileged Access Management for OT Operations
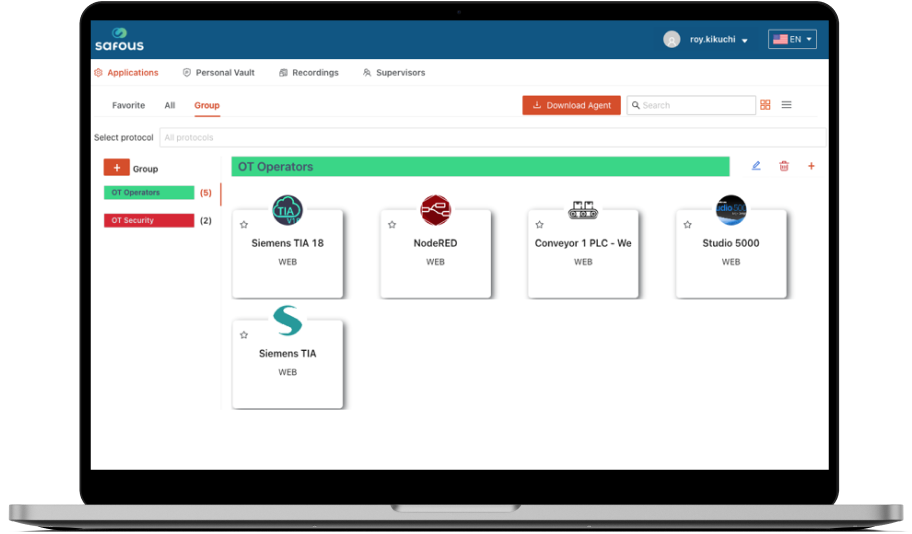
Architecture
Minimize your attack surface by giving users asset access only.
Provide identity-based asset access – not network access – to reduce the risk of hackers gaining access to your network with stolen credentials.
Verify every user and device:
Use your existing Identity Providers (IdPs) or the Cyolo IdP to validate every user and device before granting access to any resource.
Assign policies that limit asset access:
Implement policy-based Multi-Factor Authentication (MFA) and Single Sign-On (SSO) to only the applications and resources your users need for work. When work is complete, you can rescind access.
Monitor user access in real-time:
Meet reporting needs and compliance goals with access to activity logs and the ability to record sessions. Notice suspicious activity? Revoke user access in real-time.
Case Studies
Global Automaker
“Safous freed us from cumbersome VPN management and on-site access from outside vendors.”
Global Food Manufacturer
“Safous offers access management that is easy to use and doesn’t sacrifice UX while reducing attack risk.”
More Resources

The Rising Importance of IT/OT Convergence and Cybersecurity in OT

How Zero Trust Access Enhances Industrial Secure Remote Access





