COVID has prompted a major change in how we work. VPNs now connect increasingly varied locations outside of a company with the internal network, but at the same time, the cyber criminals targeting that access are getting ever craftier, and cyber-attacks on VPN vulnerabilities are never-ending. Against this backdrop, there is mounting interest in moving beyond the VPN.
1. The differences between VPN and ZTNA

When thinking about a post-VPN state, ZTNA has been garnering attention in recent years. VPNs and ZTNA might be talked about in similar ways from a network perspective, but they are actually and substantially different. Let’s take a closer look at each.
1) What is a VPN?
Broadly speaking, there are two kinds of VPN: an internet VPN, and an IP-VPN. An internet VPN uses the wider internet to route connections, while an IP-VPN uses a closed network provided by a telecommunications carrier. The IP-VPN is generally the more expensive of the two.
While the internet VPN has seen a rapid uptick in adoption as a means to enable the “work from home” approach that many companies have taken amidst the spread of COVID infections.
2) What is ZTNA?
“ZTNA” stands for “zero-trust network access”, which in turn refers to an approach to strictly controlling access in a way that places no trust in the safety of any connection regardless of whether it originates from within the company network or from outside.
ZTNA is one format of access control that Gartner proposed in 2019, based on the “Zero Trust” concept espoused by Forrester Research in 2010. This has been garnering more attention in recent years as infrastructure has loomed large in corporate thinking, prompted by the spread of cloud computing and the overall digital transformation. On a VPN, once communications have been authenticated, the user is granted full access to resources. When using ZTNA, however, the user is evaluated and access is controlled for each and every attempt to access an application or data.
One strength of this approach is the ability to greatly limit the risk of confidential information getting out due to fraudulent access by means of leaked credentials.
Related article: Blog What is ZTNA?
2. The Rise of the post-VPN

VPNs have been widely used as a means to provide remote access. However, ways of working are changing, and this is increasingly bumping up against the limits of what VPNs can do.
1) COVID leading to a fuzzing of boundaries in the workplace
Sparked by the COVID pandemic, people are working more frequently from home or other locations outside of the company office, and this is making the boundary between “inside the company” and “outside the company” much less distinct. Employees are connecting to the company’s network from a wide variety of environments and using a wider variety of devices to do so—not just PCs and laptops, but now also smartphones and tablets. This also includes employees’ personal devices, which are outside the company’s administrative control.
2) Rising internet traffic as cloud use increases
Alongside these changes in workstyle, people and companies are also using cloud services more to get their work done, things like Microsoft 365 and Zoom. The shift in so many applications used day-to-day to cloud-based services is driving a massive increase in internet traffic, sometimes overwhelming the capacity of VPN equipment. The COVID pandemic has precipitated issues like slow VPN connections or even the frequent inability to access a company’s network.
3) Frequent attacks on the vulnerabilities of legacy VPNs
As VPN use has increased, so too have older VPN devices and VPN service vulnerabilities been subject to more and more targeted attacks. Even when a patch is released for a newly discovered vulnerability, not every device has that patch applied right away, and these legacy VPNs are in the crosshairs of cyber criminals.
VPNs entail the risk that users are granted access to other resources on the network once they have been authenticated. There has also been a rise in cases where companies have had confidential information leaks due to leaked passwords or other credentials, or have become infected with ransomware.
4) Increased burden on system administrators
All of this is causing more work for system administrators, between controlling increasing amounts of network traffic, scaling out their network equipment, and the maintenance of it all. Setting a standardized security policy for the remote access environment becomes more difficult as users’ access environment itself becomes more diverse. This makes it more likely that there might be gaps in security policy or operational status between different sites.
3. Cases where VPN vulnerabilities were targeted
Here are a couple examples of cases where VPN vulnerabilities were targeted.
1) Attack on a major petroleum company’s pipeline, targeting the legacy VPN
The 2020 cyber attack on an oil pipeline was a major news story in the media. The attack was on a VPN that only used password authentication, which was insufficient to prevent unauthorized access. The criminals were able to penetrate the network and install ransomware, forcing the company to shut down primary operations for the pipeline and pay a huge ransom of $4.4 million.
2) Stolen password attack targeting the vulnerabilities of a major VPN service
A major VPN server vulnerability was discovered in 2019, and a patch was released to fix this. However, not a few companies just kept using their VPNs without applying the patch, and the IP address information of these companies wound up being traded on various dark-web sites. Attacks targeting such vulnerabilities led to several European manufacturers becoming victims of ransomware.
4. Are there any advantages in continuing to use a VPN?
Workstyles are changing, and cyber crime is growing more sophisticated. So what are the advantages in continuing to use a VPN? There is an accelerating movement around the world in the past few years to move beyond VPNs. We do not see much to recommend VPNs at this point. That said, depending on the company, the budget for buying new equipment might be limited, or there might be other challenges making it difficult to revamp operations.
Or a company just might not have a lot of remote work, or there might be only a few sites connecting to the network, in which case continuing to use VPN technology might be a viable choice. However, even in such circumstances, it is vital to maintain appropriate patch management, revise password policies, and implement multi-factor authentication, among other measures.
5.The advantages of moving from a VPN to ZTNA
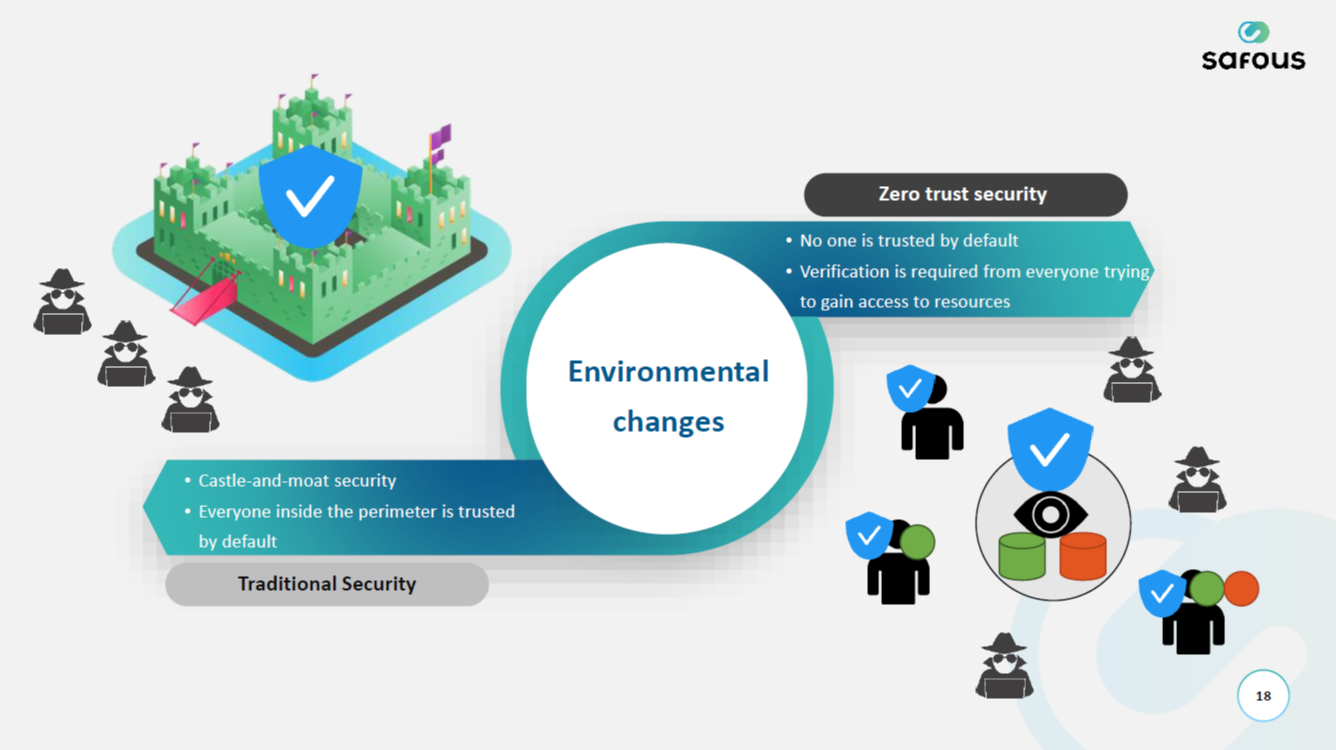
ZTNA is gaining attention as a replacement for VPNs. Let’s look at the specific positives to be gained by moving from a VPN to a ZTNA approach.
1) Limiting the risk of attacks on resources and ports
In a ZTNA setup, users (devices) generally communicate via an access point provided by a ZTNA vendor. This hides a company’s internal network resources (i.e. entry points) from the outside, reducing the risk of attack from outside as compared to using a VPN.
2) Limiting the spread of malware
With a VPN, connections happen at the network level, making it relatively easier for bad actors to spread malware and ransomware from connecting devices. With ZTNA, access is managed at the application level, making it possible to prevent the spread of malware and ransomware from connecting devices.
3) Strong and fine-grained control over authentication and authorization
As noted above, many legacy VPN setups only use password authentication, and it is also often the case that authentication strength varies from one to the next, not just for VPNs but for many different services.
Users recycling passwords or using easy-to-remember, but weak, passwords provides an opening for unauthorized access. With ZTNA, administrators can configure authentication and authorization policies at the application level that include multi-factor authentication, and they can centralize control as well.
4) Preventing network traffic jams and lags
With a VPN, all communication traffic basically happens via the company’s own internal network, so even cloud-based resources and software like Microsoft Teams are ultimately accessed via that same network. If too many employees are using the VPN at the same time, traffic bogs down and connections become laggy.
With ZTNA, once a user is authenticated, no more of their communication has to go over the company’s own internal network—the user can access resources in the cloud directly, reducing network traffic jams and preventing lagginess.
Traffic over a VPN can be reduced by using a technique called an internet breakout, but this requires planning for separate security measures. Some ZTNA solutions include SWG and CASB, improving security with no loss in ease of use.
6. Conclusion
The wide adoption of remote work has blurred the traditional lines of the workplace, and cyber criminals are honing their edges to take advantage of the change. VPN technology does indeed seem to be running up against its limitations amidst this changing environment and rising risk.
Companies need to adopt a zero-trust approach and free themselves of the border-based security model. ZTNA embodies zero-trust even right in the name, and this is becoming an ever more important technology for moving beyond VPNs.
ZTNA solutions can maintain safety while also providing a pleasant working environment. IIJ has released “Safous” as a new ZTNA solution. Please enquire for more details.
Receive the latest news, events, webcasts and special offers!
Share this
You May Also Like
These Related Stories

Blog : What is ZTNA?

Securing Remote Work in the Modern Era: Zero Trust Access in 2024




